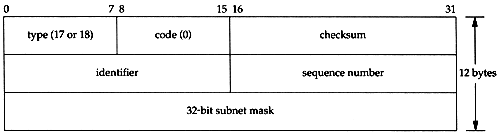
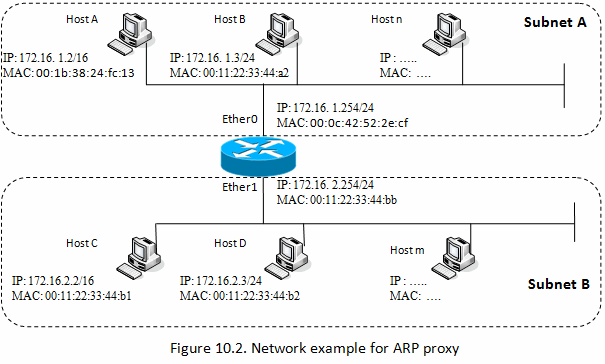
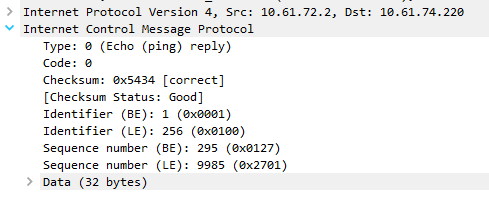
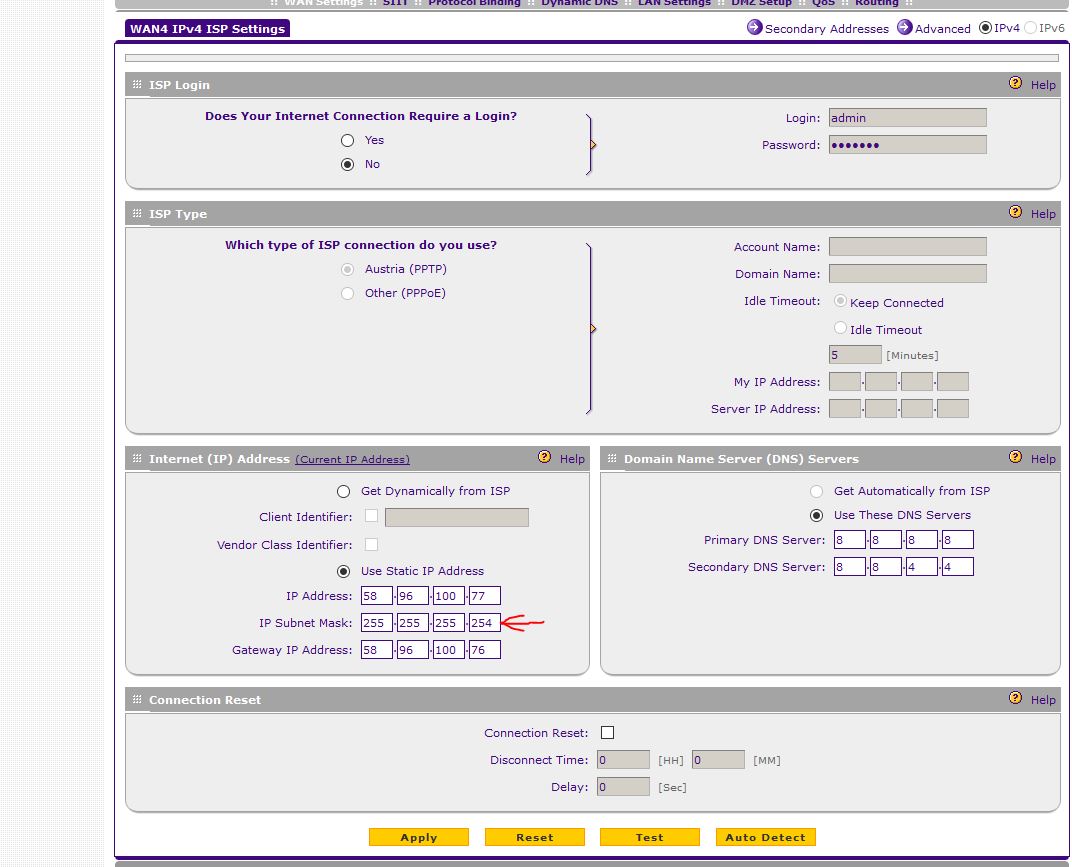
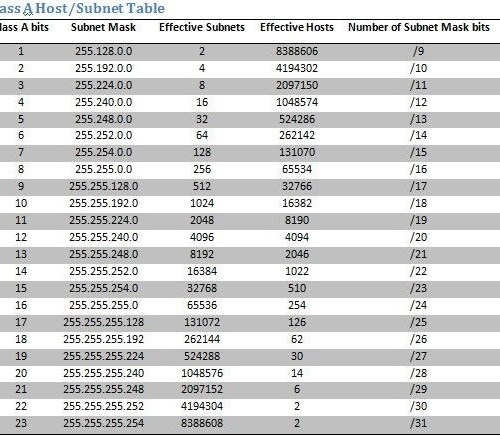
How to Statically Change IP Address, Subnet Mask, and Confirm You Can Still Send and Receive Packets. How to Enable DHCP and Communicate on a Network. How to Create and Use an
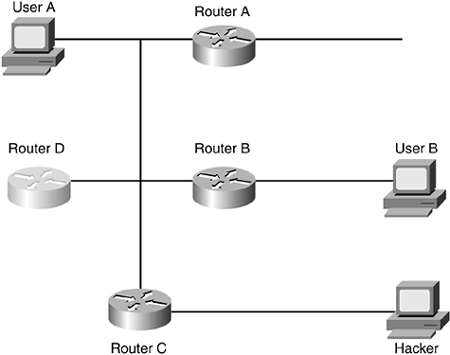
Disabling Interface Services :: Chapter 4. Disabling Unnecessary Services :: Part II: Managing Access to Routers :: Router firewall security :: Networking :: eTutorials.org

Block icmp or ping using extended acl : a cisco packet tracer lab | Learn Linux CCNA CEH IPv6 Cyber-Security Online